What Is A Cyber Threat Hunter Threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network Cyber threat hunting digs deep to find malicious actors in your environment that have slipped past your initial endpoint security defenses
Threat hunting also known as cyberthreat hunting is a proactive approach to identifying previously unknown or ongoing non remediated threats within an organization s network Subscribe to the IBM newsletter Explore the Threat Intelligence Index report Why threat hunting is important Cyber threat hunting typically takes one of the following three forms Structured In a structured hunt threat hunters look for suspicious tactics techniques and procedures TTPs that suggest potential threats Rather than approaching the data or system and looking for breachers the threat hunter creates a hypothesis about a potential attacker s method and methodically works to identify
What Is A Cyber Threat Hunter

What Is A Cyber Threat Hunter
https://www.sosecure.co.th/wp-content/uploads/2019/01/FB_IMG_1546773392024-523x740.jpg

http://tct.or.th/images/article/special_article/2565/25650717/Picture4.jpg
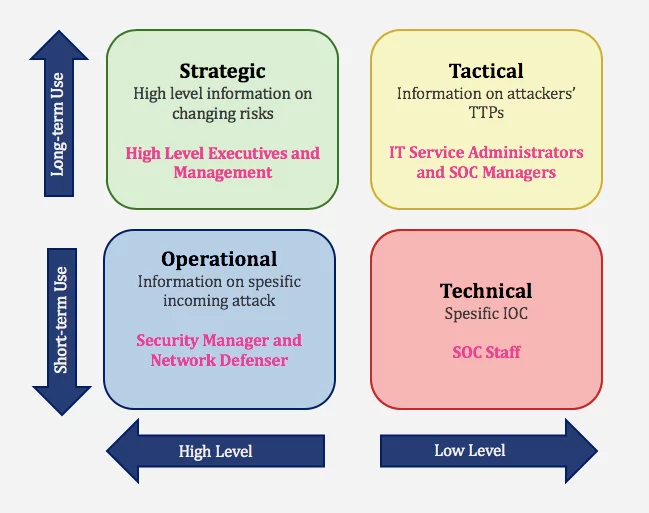
What Is Operational Cyber Threat Intelligence SOCRadar Cyber
https://socradar.io/wp-content/uploads/2021/09/tactical-cyber-threat-intelligence-definition.png
Cyber threat hunters are information security professionals who proactively and iteratively detect isolate and neutralize advanced threats that evade automated security solutions Cyber threat hunters constitute an integral part of the rapidly growing cyber threat intelligence industry Cyber threat hunting is proactively and systematically searching for signs of potential cyber threats within an organization s network or systems This can be done through manual and automated techniques such as analyzing log data conducting network scans and using threat intelligence feeds Cyber threat hunting aims to identify potential
Cyber Threat Intelligence is a focus on the analysis collection and prioritization of data to improve our understanding of threats facing a business Threat Hunting investigation types There are three core threat hunting investigation types including What is a cyber threat hunter A cyber threat hunter also called a cybersecurity threat analyst proactively identifies security incidents that may go undetected by automated security tools such as malware detectors and firewalls
More picture related to What Is A Cyber Threat Hunter

Cybersecurity Threats And Attacks All You Need To Know
https://www.stealthlabs.com/wp-content/uploads/2020/12/types-of-cybersecurity-threats.jpg

Cyber Threat Analyst Key Job Skills And Expected Salary Toolbox It
https://pimages.toolbox.com/wp-content/uploads/2020/05/05130220/Threat-Analysis.png

http://tct.or.th/images/article/special_article/2565/25650717/Picture3.jpg
Cyber threat hunting is a proactive cyber defence activity It is the process of proactively and iteratively searching through networks to detect and isolate advanced threats that evade existing security solutions 1 Threat Hunting Threat Intelligence Threat intelligence also known as cyber threat intelligence CTI is a formal process for collecting and correlating data about attempted or successful intrusions from multiple internal and external sources SIEMs often incorporate data from threat intelligence feeds to help automate rule creation
Threat hunting steps There are three phases in a proactive threat hunting process an initial trigger phase followed by an investigation and ending with a resolution or in a few cases an escalation to other teams as part of a communications or action plan Step 1 Trigger Threat hunting is typically a focused process Threat hunting is an active IT security exercise with the intent of finding and rooting out cyber attacks that have penetrated your environment without raising any alarms This is in contrast to traditional cybersecurity investigations and responses which stem from system alerts and occur after potentially malicious activity has been detected

What Is A Cyber Threat UpGuard
https://assets-global.website-files.com/5efc3ccdb72aaa7480ec8179/5f2a24e614ff3e8276b5a9d5_cyber-threat.jpg

The Top Cyber Threat To Your Network Comes From Inside Your Firewall
http://governmenttechnologyinsider.com/wp-content/uploads/2019/04/shutterstock_445417840-copy.jpg
What Is A Cyber Threat Hunter - Threat hunting is a proactive cybersecurity approach that combines digital forensics and incident response tactics to identify unknown and ongoing cyber threats that have remained undetected inside an organization s network The primary goal of threat hunting is to discover potential incidents before they negatively impact your organization